You are viewing an older version of this section. View current production version.
MemSQL Studio Security
MemSQL Studio is designed to work with MemSQL 6.5 or later and is only supported on Chrome and Firefox browsers at this time.
Authentication
MemSQL Studio is a visual SQL client that connects to your MemSQL clusters. As such, it defers to your MemSQL clusters for authentication.
Logging in
To login to a MemSQL cluster from MemSQL Studio, you must use the same username and password that you would use when connecting through an application such as the MySQL client, and the host value must either be a wildcard, or the host of the machine running MemSQL Studio. This ensures that only users with proper permissions on the proper hosts can access MemSQL clusters using MemSQL Studio. See Securing MemSQL for more details on configuring MemSQL user accounts.
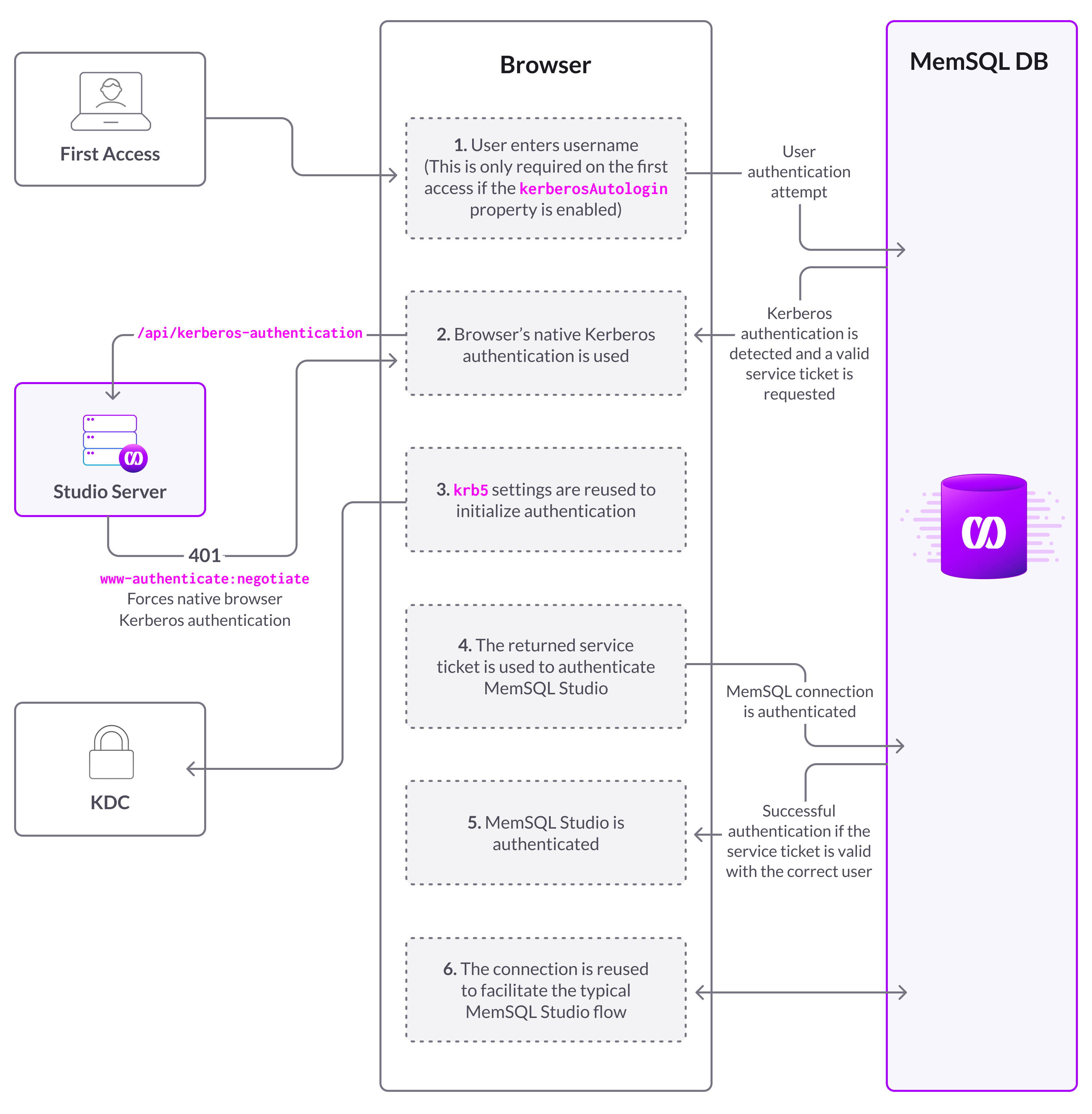
Logging in using Kerberos
As of MemSQL Studio 1.9.8, MemSQL users that have been configured with Kerberos/GSSAPI may now use Kerberos authentication to log into MemSQL Studio.
Once configured, MemSQL Studio will work as any other application using Kerberos authentication inside a browser.
Prerequisites
-
As MemSQL Studio authentication relies on MemSQL engine authentication, complete the steps in Kerberos Authentication before configuring Kerberos in MemSQL Studio.
-
(Optional) To allow MemSQL Studio to automatically log in with the current Kerberos user, set the
kerberosAutologinproperty totruein the MemSQL Studio state file. You must restart MemSQL Studio after changing this configuration.
Configuration Example
This example uses the configuration detailed in the Kerberos SPN generation section of The Chromium Projects’ HTTP authentication.
-
MemSQL Studio is served under the CNAME
auth-server.example.comand the Kerberos Realm isexample.com. -
MemSQL Studio is accessed from
auth-server.example.com. -
The browser has Kerberos configured.
-
A Kerberos Service Principal Name (SPN) of
HTTP/auth-server.example.com@EXAMPLE.COMis used for authentication. This is the default SPN generated by the browser. This SPN must be added to your KDC as a trusted new client. -
The variable gssapi_principal_name MemSQL engine variable is defined with the desired SPN (in this example,
HTTP/auth-server.example.com@EXAMPLE.COM).- This SPN is also added to the Kerberos keytab file and defined in
gssapi_keytab_path. To list the SPNs associated with a keytab, run the following on the command line:
klist -ket /path/to/name.keytab - This SPN is also added to the Kerberos keytab file and defined in
Kerberos authentication flow
The Kerberos authentication flow is depicted in the following diagram.
Running queries
Once logged in, all queries from MemSQL Studio against MemSQL clusters are run with the user’s cluster credentials. This ensures that all user permissions on the cluster are respected. As MemSQL Studio does not have any additional access to the database beyond the user’s connection, the data returned will be same as if the user was running the query from the command line.
Serving the UI with HTTPS
To serve the MemSQL Studio user interface with HTTPS, edit the MemSQL Studio configuration file to include the following two options:
HTTPSCertificateFile = "./server.crt"
HTTPSCertificateKeyFile = "./server.key"
The HTTPSCertificateFile key must point to the path of the public certificate that you’d like to use for HTTPS.
The HTTPSCertificateKeyFile must point to the path of the key file.

